-
Tweets1K
-
Followers2K
-
Following547
-
Likes135
New article by @a13xp0p0v: "Kernel-hack-drill and a new approach to exploiting CVE-2024-50264 in the Linux kernel." Alexander used his pet project kernel-hack-drill to exploit a hard race condition that received the Pwnie Award 2025. swarm.ptsecurity.com/kernel-hack-dr…
OK, ChatGPT 5 admittedly surprised me in a positive way. I threw a PNG with a (small) Python AST graph at it and told it to reverse it to Python code, and it successfully did that. I have expected it to fail hard, but here we are 🤷.
The "Critical" Chrome GPU bug (CVE-2025-9478) is suspicious. Background: Google Big Sleep recently patched a bunch of high/critical issues in privileged Chrome GPU (their new AI fuzzer). I looked at the code. All the issues require such an uncommon platform functionality, it's…
Simplified intended solution for my Windows kernel challenge at HITCON CTF 2025. github.com/scwuaptx/CTF/t… If you haven’t played this challenge yet, I encourage you to try it yourself first. github.com/scwuaptx/CTF/t… Hope everyone can learn more from our CTF.
chromereleases.googleblog.com/2025/08/stable… [N/A][436181695] High CVE-2025-9132: Out of bounds write in V8. Reported by Google Big Sleep on 2025-08-04 TL;DR: Repro extremely short, bug very easily exploitable for a renderer RCE. Big Sleep is interesting indeed :)
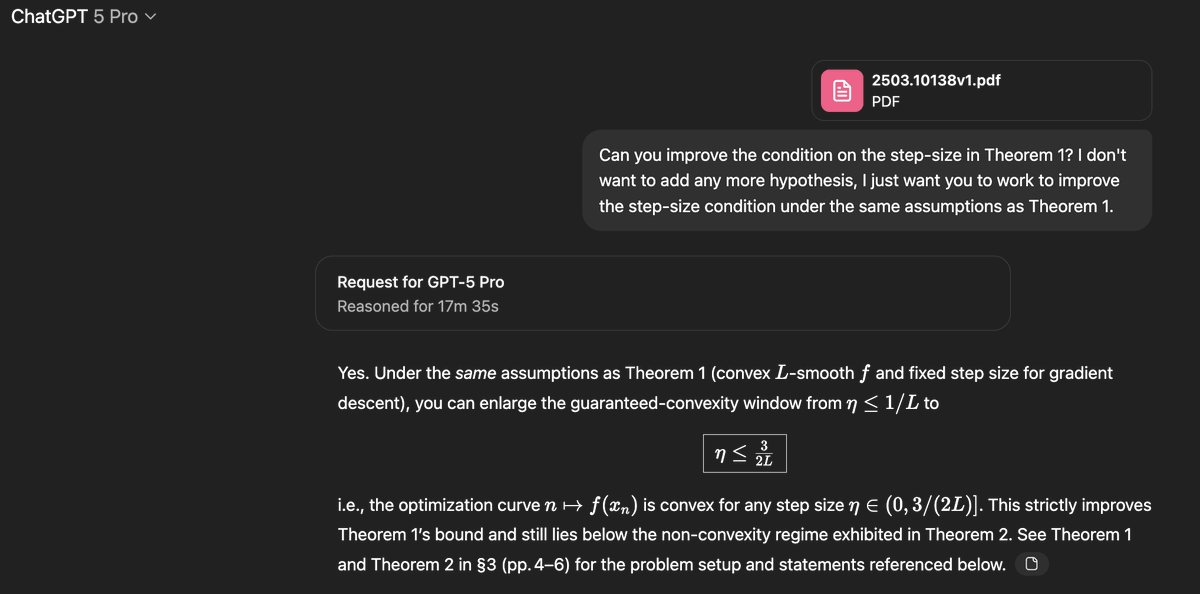
GPT-5 just casually did new mathematics. Sebastien Bubeck gave it an open problem from convex optimization, something humans had only partially solved. GPT-5-Pro sat down, reasoned for 17 minutes, and produced a correct proof improving the known bound from 1/L all the way to…
GPT-5 just casually did new mathematics. Sebastien Bubeck gave it an open problem from convex optimization, something humans had only partially solved. GPT-5-Pro sat down, reasoned for 17 minutes, and produced a correct proof improving the known bound from 1/L all the way to… https://t.co/QJ3pdZKtzH
Chrome : WebGL DrawArrays Kernel Use-After-Free (reward: $1000) crbug.com/408093267
finally got around to writing up my windows exploit from pwn2own vancouver 2024! (plus some notes about using it on xbox) exploits.forsale/pwn2own-2024/
(CVE-2025-8901)[435139154][ANGLE][Translator] Without this validation, a shader using an inout variable can write into a memory beyond the limit set by MaxDrawBuffers when shader framebuffer fetch is enabled(OOBW) chromium-review.googlesource.com/c/angle/angle/… 👀Reported by Google Big Sleep
Some personal news: I'm thrilled to be moving back to Project Zero! Specifically I'll be joining the Big Sleep project to find vulnerabilities in JavaScript engines. We've already found and reported our first vulnerability in V8 last week: issuetracker.google.com/issues/4362107…
#ESETresearch has discovered a zero-day vulnerability in WinRAR, exploited in the wild by Russia-aligned #RomCom @dmnsch @cherepanov74 welivesecurity.com/en/eset-resear… 1/7
That time when @tehjh was just reviewing a new Linux kernel feature, found a security vuln, then went on a journey to see if he could exploit it from inside the Chrome Linux Desktop renderer sandbox (spoiler: very yes) googleprojectzero.blogspot.com/2025/08/from-c…
Our latest post details how we exploited Retbleed (a CPU vulnerability) to compromise a machine from a sandboxed process and VM! Curious? 👇 bughunters.google.com/blog/624373010…
Today as part of our commitment to transparency in this space, we are proud to announce that we have reported the first 20 vulnerabilities discovered using our AI-based "Big Sleep" system powered by Gemini — goo.gle/bigsleep
We released our Fuzzilli-based V8 Sandbox fuzzer: github.com/googleprojectz… It explores the heap to find interesting objects and corrupts them in a deterministic way using V8's memory corruption API. Happy fuzzing!
So did y'all know that in arm64 Linux kernel (including Android) there is a 1:1 linear mapping of physical memory at a static non-ASLR'd virtual address? Given a physical address you can calculate the corresponding virtual address. project-zero.issues.chromium.org/issues/4342084… Anyway, happy Friday.
Good Morning! Just published a blog post diving into Windows Kernel LFH exploitation in the latest Windows 24h2 build, Focusing on controlled allocations to achieve arbitrary read/write in the kernel. r0keb.github.io/posts/Modern-(…
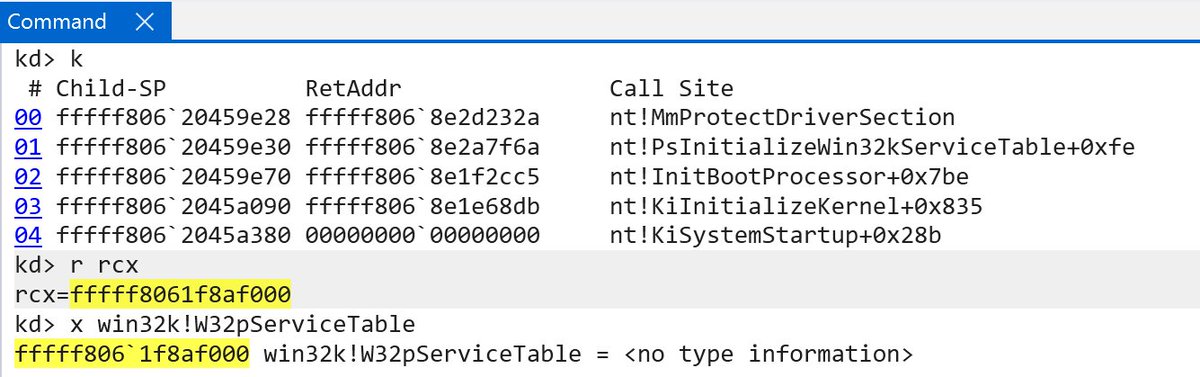
I don't know which update specifically, but in a recent update of 24H2 it looks like the Win32k system call table is protected by Kernel Data Protection (read-only SLAT entry)! I believe CI!g_CiOptions and msseccore's SecKdpSe PE section were the only things using it before.
Here is our 0day for kernelCTF🩸 - 82k bounty - quickest submission ever - all instances pwned😎 syst3mfailure.io/rbtree-family-… Disclaimer: We apologize for abusing the red black tree family. Turning grandparents against grandchildren is only acceptable in the context of pwn😤
Here is our 0day for kernelCTF🩸 - 82k bounty - quickest submission ever - all instances pwned😎 syst3mfailure.io/rbtree-family-… Disclaimer: We apologize for abusing the red black tree family. Turning grandparents against grandchildren is only acceptable in the context of pwn😤
I've discovered via code review: 2 zero-click RCE logic bugs in Linux kernel Bluetooth & userspace (late 2024). Exploitable to register rogue HID w/o auth. One allows bonding w/o confirmation, bypassing CVE-2023-45866 @marcnewlin patch. Details: ubuntu.com/security/CVE-2…

chompie @chompie1337
83K Followers 1K Following hacker, weird machine mechanic, X-Force Offensive Research (XOR)
Trend Zero Day Initia... @thezdi
83K Followers 16 Following Trend Zero Day Initiative™ (ZDI) is a program designed to reward security researchers for responsibly disclosing vulnerabilities.
Alex Plaskett @alexjplaskett
12K Followers 571 Following Security Researcher | Pwn2Own 2018, 2021, 2022, 2024 | Posts about 0day, OS, mobile and embedded security.
kylebot @ky1ebot
6K Followers 319 Following CTF player @Shellphish | PhD Student @ASU | @angrdothorse dev | Author of how2heap | Vulnerability Research Hobbyist | @[email protected]
kmkz @kmkz_security
19K Followers 2K Following Offensive Security, pom-pom girl... Who cares ?? Bourbon Offensive Security Services | BOSS
Faith 🇧🇩🇦�... @farazsth98
4K Followers 318 Following Lead Cosmos Security Engineer @zellic_io, CTFer @SuperGuesser, Prev: Android Vulnerability Research @dfsec_com
Andrey Konovalov @andreyknvl
7K Followers 783 Following Security engineer at https://t.co/027VXUlgOx. Focusing on the Linux kernel. Maintaining @linkersec. Trainings at https://t.co/D5MrxmYimS.
NiNi @terrynini38514
2K Followers 583 Following Security Researcher at @d3vc0r3 / Pwn2Own Master of Pwn (Toronto 2022) / CTFer @balsnctf
ohjin @pwn_expoit
4K Followers 445 Following I'm still hungry. I will be world-class, @[email protected]
Andy Nguyen @theflow0
61K Followers 446 Following The opinions stated here are my own, not those of my company.
Axel Souchet @0vercl0k
13K Followers 544 Following ¯\_(ツ)_/¯, blogging on https://t.co/36oOc8Mgha and posting codes on https://t.co/P83Oen94Rc.
KT @koczkatamas
4K Followers 926 Following Security Engineer @ Google (personal account, opinions are my own!). ex-Tresorit. Ex-captain of @SpamAndHex CTF team.
SinSinology @SinSinology
13K Followers 674 Following Pwn2Own 20{22,23,24,24.5,25,25.5}, i look for 0-Days but i find N-Days & i chase oranges 🍊
INSU YUN @insu_yun
2K Followers 603 Following Associate Professor (Untenured) at KAIST EE #KAIST #HackingLab #GoN
Bhagirathsinh Vala @Vala9007
47 Followers 1K Following Dad first 👨👧 | Building apps (iOS & Android) | Leading engineers | Into AI, health tech & global affairs 🌍 | Caffeine-dependent lifeform ☕
Allele Security Intel... @alleleintel
711 Followers 503 Following Allele Security Intelligence is an independent company specializing in Information Security research.
Hacktivity @hacktivityconf
4K Followers 463 Following #HACKTIVITY is the biggest event of its kind in Central & Eastern Europe. Started and founded in 2003. Main theme: hacking, cyber&IT sec, AI,crypto, innovation.
lvzhouhang @lzhouhang
26 Followers 438 Following
Ahmed Y. Elmogy @AhmedYElmogy
41 Followers 1K Following Independent web security researcher and bug bounty hunter.
MicrosVuln @microsvuln
2K Followers 1K Following Vulnerability under the 🔬Microscope, Dating security mitigations, breaking them up in the end ...
Yeongjin Jang (blue90... @blue9057
2K Followers 3K Following Principal Engineer at #SamsungResearchAmerica. Member of #TeamAtlanta. DEF CON CTF Winner. My tweets do not reflect the view of Samsung/SRA. A sponsor of 🐻
Jich @Jich_
7 Followers 277 Following InfoSec wannabe. Always busy looking at 14,000,605 possibilities
Abhinav Kumar @HelNull
0 Followers 54 Following
Advance-sec @advance_sec0
766 Followers 705 Following Advance-sec platform: is one of the top leaders in research and acquisition of vulnerabilities and 0day exploits. Email: [email protected] Wire: @advance_sec
Alan @Alan1144908
1 Followers 315 Following
P I M P @PIMP149078
36 Followers 1K Following
Huy Nguyễn @HuyNg1273273
0 Followers 4 Following
比个心 @vbigthing
92 Followers 4K Following
0xTen @_0xTen
1K Followers 843 Following android/linux kernel @vigilant_labs • prev blockchain @osec_io • ctf/pwn @cor_ctf + @eltctfbr
Scott Bauer @ScottyBauer1
3K Followers 594 Following I find 0 days. Android/Linux Kernel/Crap written in C. Will trade 0 days for bottles of DRC
d4rkc0nd0r @d4rkc0nd0r
242 Followers 498 Following
combab0 @combab0
577 Followers 6K Following
Filip Dragovic @filip_dragovic
7K Followers 1K Following My research unless stated otherwise. My opinions are my own and do not represent the views of my employer.
hamaccount @hamaccount
16 Followers 2K Following
Victor4XCTF @Victor4Xctf
1 Followers 371 Following
f3YK2MDZ3CRKeQD @f3YK2MDZ3CRKeQD
0 Followers 75 Following
陈维政 @SB6lvoZjVL83942
0 Followers 1 Following
no_r0llback @0xmadvise
1K Followers 383 Following rekcah - tnednepedni rehcraeser - 8v & xunil lenrek
v6r @V6R__
3K Followers 489 Following
bik0t @bik0t
21 Followers 578 Following
Amalia Radoi @AmaliaRado56600
5 Followers 359 Following
pwn2ooown @pwn2ooown
84 Followers 1K Following Pwn / ♥️Red Team / OSCP+ / Not affiliated with pwn2own competition / CTF with B33F 50μP & @thehackerscrew1 / opinions are on my own
Mutai @Blu_SOC
32 Followers 932 Following
nedwill @NedWilliamson
16K Followers 551 Following Tesla {Autopilot, Dojo}; Previously Google Security; PPP for life; SockPuppet, Soundhax, Speedcubing
Reeve Musk @reeve_musk0011
28 Followers 1K Following Personal Interactive Account Reaching Out To My Supporters Randomly On X
chompie @chompie1337
83K Followers 1K Following hacker, weird machine mechanic, X-Force Offensive Research (XOR)
Trend Zero Day Initia... @thezdi
83K Followers 16 Following Trend Zero Day Initiative™ (ZDI) is a program designed to reward security researchers for responsibly disclosing vulnerabilities.
cts🌸 @gf_256
61K Followers 820 Following Co-founder and hacker @zellic_io & @pb_ctf | https://t.co/nlNai6iiMP | 24 Intern @egirl_capital slow to reply to DMs
Project Zero Bugs @ProjectZeroBugs
35K Followers 0 Following A bot that posts the latest blog posts and disclosures from Google's Project Zero
starlabs @starlabs_sg
9K Followers 20 Following A Singapore company that discovers vulnerabilities to help customers mitigate the risks of cyber attacks. Organisers of @offbyoneconf
Chromium Disclosed Se... @BugsChromium
8K Followers 0 Following Tweets publicly disclosed bugs in Chromium. Not an official Google product. Run by @SecurityMB. Mastodon: @[email protected]
Alex Plaskett @alexjplaskett
12K Followers 571 Following Security Researcher | Pwn2Own 2018, 2021, 2022, 2024 | Posts about 0day, OS, mobile and embedded security.
kylebot @ky1ebot
6K Followers 319 Following CTF player @Shellphish | PhD Student @ASU | @angrdothorse dev | Author of how2heap | Vulnerability Research Hobbyist | @[email protected]
Ivan Fratric 💙💛 @ifsecure
18K Followers 207 Following Security researcher at Google Project Zero. Author: Jackalope, TinyInst, WinAFL, Domato. PhD. Tweets are my own. Backup @[email protected]
Ptrace Security GmbH @ptracesecurity
59K Followers 867 Following Empowering IT Security Professionals through Hands-On Online Courses.
Faith 🇧🇩🇦�... @farazsth98
4K Followers 318 Following Lead Cosmos Security Engineer @zellic_io, CTFer @SuperGuesser, Prev: Android Vulnerability Research @dfsec_com
simo @_simo36
7K Followers 116 Following
Samuel Groß @5aelo
24K Followers 501 Following Working on Project Zero, Big Sleep, and V8 Security. Personal account. Also @[email protected] and https://t.co/aVitnPjBie
Haifei Li @HaifeiLi
8K Followers 151 Following For contact in the security community. NOTE: All the tweets are totally my personal opinions, not about any of my current employer stuff.
SSD Secure Disclosure @SecuriTeam_SSD
24K Followers 2 Following SSD provides the support you need to turn your experience uncovering security vulnerabilities into a highly paid career. [email protected]
Alisa Esage Шевч�... @alisaesage
38K Followers 101 Following Independent Hacker & Researcher, Owner of Zero Day Engineering @zerodaytraining • Pronounced ‘is edge’
Software Engineering @ComputerPapers
2K Followers 6 Following New Software Engineering submissions to https://t.co/vxDuY4St9Z (not affiliated with https://t.co/vxDuY4St9Z)
Wil Gibbs @cl4sm
524 Followers 241 Following @ASU Sefcom PhD Student | @Shellphish Captain Emeritus | AIxCC Shellphish Team Lead | pwn and rev is where it’s at | 日本語🤏
Yeongjin Jang (blue90... @blue9057
2K Followers 3K Following Principal Engineer at #SamsungResearchAmerica. Member of #TeamAtlanta. DEF CON CTF Winner. My tweets do not reflect the view of Samsung/SRA. A sponsor of 🐻
Security Bug Aggregat... @BugsAggregator
1K Followers 1 Following Aggregate Chromium disclosed security bugs.
emma @carrot_c4k3
4K Followers 278 Following cyber torture pioneer. bug bounty billionaire. most controversial pwn2own winner (contested). en🇺🇸/ru🇰🇿. she/her 🏳️⚧️
XBOW @Xbow
10K Followers 6 Following Bringing AI to offensive security by autonomously finding and exploiting web vulnerabilities. Watch XBOW hack things: https://t.co/D5Mco1u8zM
Tim Becker @tjbecker_
2K Followers 349 Following Security Researcher at @theori_io. Flag capturer at @PlaidCTF. Cryptography enjoyer.
Team Atlanta @TeamAtlanta24
676 Followers 26 Following 🔥AIxCC Winner Team | Georgia Tech, Samsung Research, KAIST, POSTECH | 🚀Building next-gen AI-driven bug finding & fixing systems | CRS Atlantis 🌊
Offensive AI Con @OffensiveAIcon
637 Followers 12 Following The first conference dedicated to exploring the offensive use of AI. Request an invite at our site. #OffensiveAICon Oct 5-8, 2025 | Oceanside, San Diego
deepsec.cc @deepsec_cc
254 Followers 0 Following
Rolf Rolles @RolfRolles
14K Followers 357 Following Static reverse engineering, deobfuscation, program analysis and formal verification, training, mathematics, compilers, functional programming, etc.
Gerrard Tai @gerrard_tai
183 Followers 522 Following ex csgo pro for team "Counter-Terrorists" | pwn with @seetf_sg
Kevin Colley @kjcolley7
69 Followers 39 Following Product Security Engineer. Former President of @HackUCF. I like iOS jailbreaking, game modding, CTF competitions, and snowboarding.
Renan Rios @hyhy_100
220 Followers 294 Following Weeb bounty hunter 🇧🇷, 2024 Top 20 Chrome VRP Researcher. Interested in browser/kernel security, GFX and AI driven text games. Miqu!
watchTowr @watchtowrcyber
9K Followers 13 Following watchTowr enables organizations to get ahead of in-the-wild exploitation with Preemptive Exposure Management technology.
kiddo @kiddo_pwn
971 Followers 387 Following Independent Security Researcher | Pwn2Own (24🇮🇪 / 25🏎️)
TyphoonCon🌪️ @typhooncon
8K Followers 4 Following TyphoonCon is an annual all Offensive Security Conference, taking place May 25-39, 2026 in Seoul, South Korea 🌪️
Volodya @volodiyah
613 Followers 448 Following Security Engineer interested in Program Analysis with applications in (de)obfuscation, antivirus evasion or vulnerability research.
SinSinology @SinSinology
13K Followers 674 Following Pwn2Own 20{22,23,24,24.5,25,25.5}, i look for 0-Days but i find N-Days & i chase oranges 🍊
Kevin2600 @Kevin2600
11K Followers 57 Following
HBh25Y @HBh25Y
54 Followers 299 Following
peterpan0927@infosec.... @Peterpan980927
2K Followers 352 Following Mobile Security Researcher @starlabs_sg
Danis Jiang @danis_jiang
3K Followers 1K Following Yuhao Jiang / former ctfer @ Vidar-Team / Security Researcher @ Ant Group Light-Year Security Lab / GeekPwn 2022 / Pwnie Awards 2023 / Tianfu Cup 2023
Crowdfense @crowdfense
3K Followers 1K Following Crowdfense is the world-leading research hub and acquisition platform for zero-day exploits and vulnerability research. We offer the highest bounties
Man Yue Mo @mmolgtm
5K Followers 78 Following Security researcher at GitHub Security Lab. Tweets/views/opinions are my own.
REverse_Tactics @Reverse_Tactics
795 Followers 2 Following Software reverse engineering & vulnerability discovery company.
luckyu @uuulucky
577 Followers 233 Following
exploits.club @exploitsclub
2K Followers 110 Following A VR, RE, and Exploit Dev weekly newsletter | Join the club Contact: [email protected]
GEEKCON @GEEKCONTOP
524 Followers 62 Following Initiated by DARKNAVY. New @GeekPwn. Globally unmatched security geek event, promoting the visualization & measurable value of security ecosystem capabilities.
1377 High-yield Nukes @buptsb
2K Followers 1K Following
zeze ⛈️ @zeze7w
211 Followers 356 Following @TeamT5_Official Research Engineer / @HacksInTaiwan Staff
DARKNAVY @DarkNavyOrg
2K Followers 50 Following Cybersecurity enthusiasts from DARKNAVY. Achieve, Analyze, Attack *Oops.
SYSPWN @syspwnx
264 Followers 29 Following SysPWN : A place to learn more about Vulnerability Research and make yourself ready for world-class hacking competitions
Rado RC1 @RabbitPro
5K Followers 658 Following Exploitation, hardware, embedded, reverse engineering, automotive security. Pwn2Own Master of Pwn Flashback team (@FlashbackPwn).
vdehors @vdehors
1K Followers 214 Following