Arris Huijgen @bitsadmin
Windows Offensive Security Enthusiast 🤠 Blog: https://t.co/CAwdjs2rKS GitHub: https://t.co/YG2YOxfosm bitsadmin.com Amsterdam, The Netherlands Joined March 2016-
Tweets231
-
Followers2K
-
Following108
-
Likes265
[Research] Starting Chrome Exploitation with Type Confusion 101 ^-^☆ Part 1.(EN) hackyboiz.github.io/2025/07/01/OUY… Ever wondered how Chrome's V8 engine actually runs JavaScript, and how those internals can lead to security issues like Type Confusion? In this post, I break down the V8…
🚀 We just released my research on BadSuccessor - a new unpatched Active Directory privilege escalation vulnerability It allows compromising any user in AD, it works with the default config, and.. Microsoft currently won't fix it 🤷♂️ Read Here - akamai.com/blog/security-…
What if you skipped VirtualAlloc, skipped WriteProcessMemory and still got code execution? We explored process injection using nothing but thread context. Full write-up + PoCs: blog.fndsec.net/2025/05/16/the…
Blogpost from my colleague about what’s still possible with recently published COM/DCOM toolings, Cross Session Activation and Kerberos relaying 🔥 r-tec.net/r-tec-blog-win…
ProxyBlob is alive ! We’ve open-sourced our stealthy reverse SOCKS proxy over Azure Blob Storage that can help you operate in restricted environments 🔒 🌐 github.com/quarkslab/prox… Blog post for more details right below ⬇️
ProxyBlob is alive ! We’ve open-sourced our stealthy reverse SOCKS proxy over Azure Blob Storage that can help you operate in restricted environments 🔒 🌐 github.com/quarkslab/prox… Blog post for more details right below ⬇️
Cool, novel, lateral movement technique by @william_knows by dropping a .dll file on a remote host obtaining code execution! 💡
Cool, novel, lateral movement technique by @william_knows by dropping a .dll file on a remote host obtaining code execution! 💡 https://t.co/fb9yXQi9Hn
I just published a blog post where I try to explain and demystify Kerberos relay attacks. I hope it’s a good and comprehensive starting point for anyone looking to learn more about this topic. ➡️decoder.cloud/2025/04/24/fro…
The S is for Security. How to use WinRMS as a solid NTLM relay target, and why it’s less secure than WinRM over HTTP. By @Defte_ Writeup: sensepost.com/blog/2025/is-t… PR to impacket: github.com/fortra/impacke… Demo: youtu.be/3mG2Ouu3Umk
We’re glad to announce we released Soxy!🚀 A Rust-powered suite of services for Citrix, VMware Horizon & Windows RDP. Red teams & pentesters can use it to pivot for deeper access. Get the tool and more details: 🔗 github.com/airbus-seclab/…
Your laptop was stolen. It’s running Windows 11, fully up-to-date, device encryption (BitLocker) and Secure Boot enabled. Your data is safe, right? Think again! This software-only attack grabs your encryption key. Following up on our #38C3 talk: neodyme.io/blog/bitlocker…
How to bypass BitLocker encryption on Windows 11 noinitrd.github.io/Memory-Dump-UE…
Just released SCCMHound! A BloodHound collector for SCCM. SCCMHound allows both attackers and defenders to construct BloodHound datasets using the vast amount of information that is stored/retrievable through SCCM. Feel free to take it for a spin! github.com/CrowdStrike/sc…
A new fun way to set shadow credentials posts.specterops.io/attacking-entr…
Ever wondered how CryptProtectMemory with the CRYPTPROTECTMEMORY_SAME_PROCESS flag worked, or if encrypted blobs could be decrypted without code injection ? I wrote a blogpost about it: blog.slowerzs.net/posts/cryptdec…
Per suggestion of @jelleverg, added the memory-efficient json2csv.py script to the dir2json repository. As a bonus also added dir2csv.py to convert the output of cmd.exe's dir /s /a command to csv. Useful to avoid PowerShell's logging mechanisms 😉 Enjoy!
Per suggestion of @jelleverg, added the memory-efficient json2csv.py script to the dir2json repository. As a bonus also added dir2csv.py to convert the output of cmd.exe's dir /s /a command to csv. Useful to avoid PowerShell's logging mechanisms 😉 Enjoy! https://t.co/PviGZukO8P
Because in the 24H2 release of Windows 11 vbscript is being phased out, the missingkbs utility for Windows Exploit Suggester - Next Generation (#WESNG) is now also available in PowerShell flavor! 🙂 🎯 Check out missingkbs.ps1 @ github.com/bitsadmin/wesng
Because in the 24H2 release of Windows 11 vbscript is being phased out, the missingkbs utility for Windows Exploit Suggester - Next Generation (#WESNG) is now also available in PowerShell flavor! 🙂 🎯 Check out missingkbs.ps1 @ github.com/bitsadmin/wesng https://t.co/IL277lqdbm
Dropping a new initial access technique via RDP that I dubbed "Rogue RDP". Use malicious .RDP files to bypass email/servers/security gateways and then run code to binary plant/exfil from your own RDP server, blinding EDR. Bonus: Target runs HyperV? RCE! blackhillsinfosec.com/rogue-rdp-revi…
Hello: I'm your ADCS server and I want to authenticate against you. My latest Post and PoC are out. You can read it here: decoder.cloud/2024/02/26/hel… Enjoy :)
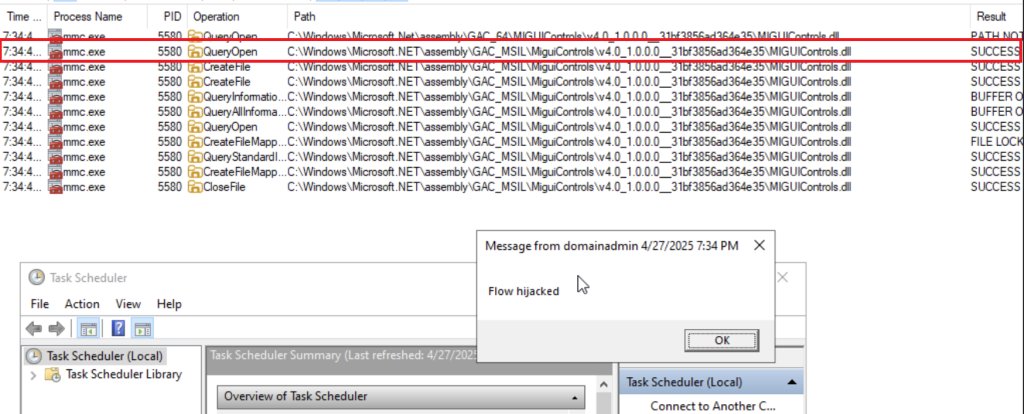
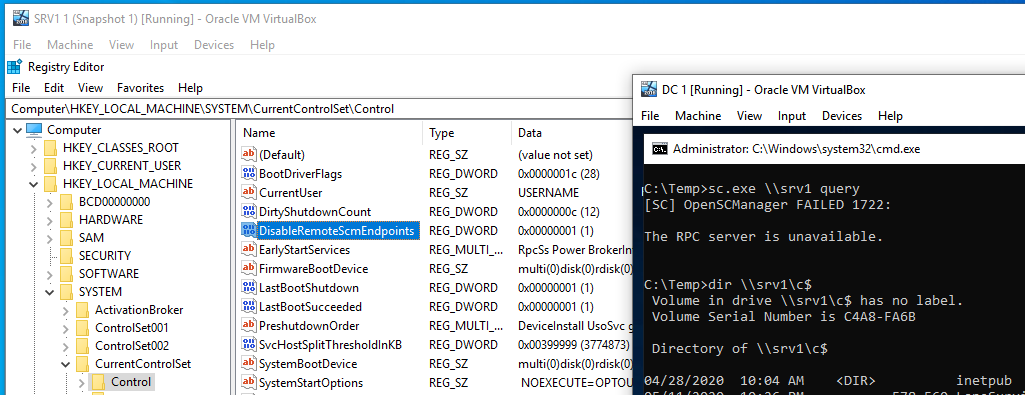
Eliminate huge part of lateral movement scenarios with one command: "reg.exe add HKLM\SYSTEM\CurrentControlSet\Control /v DisableRemoteScmEndpoints /t REG_DWORD /d 1" It will make Service Control Manager deaf to remote management. Everything else works properly.

John Hammond @_JohnHammond
298K Followers 3K Following Cybersecurity Researcher @HuntressLabs || Just Hacking Training @JustHackingHQ w/ @ethicalhacker || https://t.co/UtsNJiyQtS || https://t.co/narO3sz7y6
SwiftOnSecurity @SwiftOnSecurity
405K Followers 9K Following computer security person. former helpdesk.
Marc Smeets @MarcOverIP
5K Followers 434 Following Does a thing or two with red teaming @OutflankNL | part time race and drift car instructor
Cas van Cooten @chvancooten
10K Followers 673 Following Benevolently malicious offensive security enthusiast || OffSec Developer & Malware Linguist || NimPlant & NimPackt author || @ABNAMRO Red Team
n00py @n00py1
13K Followers 963 Following Retweeter of InfoSec/Offsec/Pentest/Red Team. Occasional blogger/Independent security research.
DebugPrivilege @DebugPrivilege
40K Followers 2K Following Windows Nerd | Ex-MSFT | Microsoft MVP in Windows | Interested in Security, Debugging, and Windows Internals.
an0n @an0n_r0
13K Followers 725 Following CRT(E|O|L) | OSCP | @RingZer0_CTF 1st (for 2yrs) | HackTheBox Top10 | RPISEC MBE | Flare-On completer | GoogleCTF writeup winner | SSD research | Math MSc |🇭🇺
Olaf Hartong @olafhartong
17K Followers 965 Following @FalconForceTeam | researcher with a camera | Microsoft MVP | Snow man role model
sn🥶vvcr💥sh @snovvcrash
12K Followers 488 Following Sr. Penetration Tester / Red Team Operator @ptswarm :: Author of the Pentester’s Promiscuous Notebook :: He/him :: Tweets’re my pwn 🐣
Samir @SBousseaden
25K Followers 1K Following Detection Engineering | Elastic Security Mastodon: @[email protected]
Swissky @pentest_swissky
20K Followers 2K Following RedTeam | Pentest Author of PayloadsAllTheThings & SSRFmap https://t.co/w1ZLRqoafG
duskxy @duskxy
47 Followers 1K Following
Fabricio Aranda @fabricioarandaz
22 Followers 374 Following Publish your dynamic content management system sites as static so your site will be secure, faster & scalable. Supports WP, Joomla and Drupal.
foneun @foneun5363
0 Followers 42 Following
yolosec @yolosec257299
0 Followers 44 Following
Gabi @Blitz0p3
26 Followers 534 Following Security Consultant. Purple Teaming. Adversary Simulations. Physical Security. International Relations enthusiast. 🥷⚡
zhiwar @Zhiwarkermashan
53 Followers 175 Following Zagros Eagle We will die on our feet, but we will never live on our knees. سابقا کامپیوتر شریف مهندس امنیت درونگرا ( آدمش باشه برونگرا) اهل کمپ و پیاده روی
Meruem @Meruem49839142
169 Followers 8K Following
James Ibrahim @JamesIb54140322
55 Followers 3K Following
NIMA NIKJOO @N_Nikjoo
956 Followers 1K Following Security consultant, Threat intelligence, Malware analyst. Exploit Developer. Ex-Political-Security (IRGC & MOIS) prisoner in the Islamic Republic Regime.
keyboardcrunch @keyboardcrunch_
7 Followers 144 Following Security Engineer focused on endpoint security related shenanigans.
Mohamed Maslouh 🇵�... @MedMaslouh
137 Followers 2K Following
classic @classic225703
43 Followers 574 Following
t0xch4 @t0xch4_
4 Followers 663 Following
🇪🇸 @researcher_ESP
17 Followers 961 Following
Ojaswi Kumar Mishra�... @0xojaxwi
74 Followers 2K Following Old-school Malware & Offensive Security REsearcher | ⚡Kernel Pwner⚡
Agrippa @4grippa
0 Followers 238 Following
Mathew @Mathew3743
17 Followers 621 Following Full-Stack Developer | WFH @ 9X Technology, Dubai | Mechanical Engg '23 ➡️ Tech Enthusiast | Always Learning and Always moving
Hootch @Hootchenstein
9 Followers 645 Following
Ochopelocho @Ochopelocho32
12 Followers 742 Following
BluP3gu1n @BluP3gu1n
19 Followers 260 Following Hacker and shenanigans operator. I tend to hang in places you aren’t supposed to go.
unverifred @differenziagite
185 Followers 4K Following
Tiến Đạt Đỗ @Tint1282208
2 Followers 265 Following
٢ @tlxac
47 Followers 2K Following
Oghenetega Godwin @itztycon
390 Followers 8K Following A backend engineer• Software intern and Product marketer @dextroux (https://t.co/5daIyamICt)• Founder of @issocorp. Computer Science Student @uniben
1 @8_billions
72 Followers 782 Following
MalakaBudala @MalakaBudala6
1 Followers 99 Following
invulnerablewaste @invulnerwaste
0 Followers 2K Following
Udayveer Singh @m4lici0u5
2K Followers 4K Following Offensive Security | Red Teamer | Learning MalDev | CRTL | OSEP | OSWP | CRTO | CARTP | CRTE | CRTP | CESP-ADCS | eJPT
MAHmoudElarbawy @mahmoudElarbawy
28 Followers 1K Following
比个心 @vbigthing
93 Followers 4K Following
Ryuga Dx @Ryuga0x
7 Followers 361 Following
Arazu @Arazu_berez
12 Followers 192 Following
Durga Mishra @durgabaps
63 Followers 2K Following
MrFollany @MrFollany
22 Followers 192 Following
The James @t1gerp4w
2K Followers 5K Following Experienced Security Consultant. Who art thou?.. Virtual Space Force and Deplorable - at 7.83 Hz, 432 Hz but strive for 528 Hz. JohnJohn
Florian Roth ⚡️ @cyb3rops
206K Followers 3K Following Head of Research @nextronsystems #DFIR #YARA #Sigma | detection engineer | creator of @thor_scanner, Aurora, Sigma, LOKI, YARA-Forge | always busy ⌚️🐇 | vi/vim
Florian Hansemann @CyberWarship
84K Followers 47 Following Father, Founder @HanseSecure, Pentesting, Student, ExploitDev, Redteaming, InfoSec & CyberCyber; -- Mastodon: https://t.co/KFSKYUN98M
Adam Chester 🏴�... @_xpn_
36K Followers 501 Following Hacker for Hire at @SpecterOps | Blog at https://t.co/tjfTOllCEu | Insta at https://t.co/PqR6CZPwjl
DirectoryRanger @DirectoryRanger
35K Followers 96 Following This account assembles and disseminates information related to Active Directory and Windows security.
Grzegorz Tworek @0gtweet
36K Followers 2K Following My own research, unless stated otherwise. Not necessarily "safe when taken as directed". GIT d- s+: a+ C++++ !U !L !M w++++$ b++++ G-
Dirk-jan @_dirkjan
28K Followers 206 Following Hacker at @OutsiderSec. Researches AD and Azure (AD) security. Likes to play around with Python and write tools that make work easier.
Marc Smeets @MarcOverIP
5K Followers 434 Following Does a thing or two with red teaming @OutflankNL | part time race and drift car instructor
Oliver Lyak @ly4k_
9K Followers 265 Following Yet another security researcher 🔦 Github: https://t.co/7WFOFz17KI
Dominic Chell 👻 @domchell
18K Followers 540 Following Just your friendly neighbourhood red teamer @MDSecLabs | Creator of /r/redteamsec | https://t.co/3k3EBAZqGd | https://t.co/KwO2OwDOkl
DebugPrivilege @DebugPrivilege
40K Followers 2K Following Windows Nerd | Ex-MSFT | Microsoft MVP in Windows | Interested in Security, Debugging, and Windows Internals.
b33f | 🇺🇦✊ @FuzzySec
33K Followers 1K Following 意志 / Antiquarian @ IBM X-Force / t501 / Ex-TORE ⚔️🦅 / I rewrite pointers and read memory / AI Psychoanalyst / Teaching @CalypsoLabs
Samir @SBousseaden
25K Followers 1K Following Detection Engineering | Elastic Security Mastodon: @[email protected]
Stephan Berger @malmoeb
28K Followers 1K Following Head of Investigations @InfoGuardAG https://t.co/A5lnFAu7eX
Will Dormann is on Ma... @wdormann
26K Followers 1K Following I play with vulnerabilities and exploits. I used to be here on Twitter but now I'm here: @[email protected] https://t.co/hXggdAVkSQ
x86matthew @x86matthew
21K Followers 189 Following C / asm / system emulation / reverse engineering. @the_secret_club
🥝🏳️🌈 Be... @gentilkiwi
62K Followers 286 Following A kiwi coding mimikatz & kekeo github: https://t.co/eS3LVgU6i0 Head of security services @banquedefrance Tweets are my own and not the views of my employer
Cn33liz @Cneelis
13K Followers 598 Following Red teamer @ Outflank. Passionate about networking and cybersecurity | father of two superheroes.
The Hacker News @TheHackersNews
932K Followers 2K Following The #1 trusted source for cybersecurity news, insights, and analysis — built for defenders and trusted by decision-makers.
Linux Handbook @LinuxHandbook
146K Followers 68 Following Learn to use Linux commands, SysAdmin tools, Self-hosting, Docker and other DevOps stuff with us.
Orange Cyberdefense's... @sensepost
9K Followers 322 Following Work like hell, Share all you know, Abide by your handshake, Have fun. - Dan Geer
Steve Borosh @rvrsh3ll
1K Followers 613 Following The future is not set. There is no fate, but what we make for ourselves. - John Connor
S4ntiagoP @s4ntiago_p
3K Followers 852 Following Infosecing at @MDSecLabs, ex @CoreSecurity CVEs: -1
John Frankel 🚶�... @john_frankel
23K Followers 2K Following Longtime tech investor. Early stage venture capitalist. builder. Love working with energetic entrepreneurs working to change the world.
Peter Winter-Smith @peterwintrsmith
6K Followers 3K Following Security researcher & implant developer @mdseclabs; developing SAST @wsastsupport; malware, code analysis, appsec, cryptography. Trying to follow Christ.
Blaklis @Blaklis_
11K Followers 70 Following Security researcher - my researchs will be on https://t.co/2PnyCvqAIm Inactive X account.
Philip Elder @MPECSInc
2K Followers 374 Following Microsoft MVP '09-Present. We design & build HA solutions for on-premises, data centre, & hybrid. Workload Migration Specialists. Active Directory Security.
clearbluejar @clearbluejar
2K Followers 360 Following Security Researcher | Founder @clearseclabs | Research | Learn | Write | Code | Repeat | https://t.co/0lF2NPtj5H | Author of #ghidriff | #patchdiffing
Gi7w0rm @Gi7w0rm
18K Followers 801 Following Threat Intelligence Analyst | See my Linktree for other socials | In case I post false intel, contact me! Support me: https://t.co/5WgDqr0K8p 🇪🇺🇩🇪🇺🇦🌈
topotam @topotam77
4K Followers 689 Following All I know is that I know nothing. I like Windows, Active Directory and IoT/Hardware hacking. "Responsable mais pas coupable" de PetitPotam
TrainSec Academy - Wh... @TrainSec
706 Followers 80 Following Learn Windows Internals, Malware Analysis, Malware Development, Hardware Hacking & Code Development from @zodiacon, @MalFuzzer & @The_H1tchH1ker
BlueHat IL @BlueHatIL
6K Followers 532 Following
windbgtips @windbgtips
4K Followers 1 Following A collection of some tips & tricks for the world's best debugger
Marat Nigmatullin @_mnigma_
86 Followers 123 Following Hacking & Researching @falconforceteam | Ex-Unit 42
Cedric Van Bockhaven @c3c
913 Followers 344 Following
VbScrub @VbScrub
1K Followers 44 Following VB. Active Directory. HTB Machines. These are a few of my favourite things.
mr.d0x @mrd0x
44K Followers 296 Following Security researcher | Co-founder https://t.co/QxBlzp9A8w | https://t.co/zqMXQRZjQN | https://t.co/Fq7WSqTBva | https://t.co/eKezFcO6nd
Carsten @0xcsandker
2K Followers 174 Following Security enthusiast, Likes Windows Internals, AD & Entra — https://t.co/mVVbfkO7IO
Clément Labro @itm4n
7K Followers 166 Following Pentest & Windows security research (I stopped using this account in December 2022) ➡ Mastodon: @[email protected]
Harpreet Singh @TheCyb3rAlpha
120 Followers 271 Following Deloitte Red Team | Pen Tester | Author | Otaku
Andrea P @decoder_it
8K Followers 290 Following Security Consultant @semperistech . Independent Security Researcher. Cyclist & Scubadiver. MSRC MVR 2022. "So di non sapere"
Antonio Cocomazzi @splinter_code
9K Followers 327 Following offensive security - windows internals | BlueSky: https://t.co/ytvJCoaF2c | Mastodon: https://t.co/hNIHa6L14d
Cobalt Strike @_CobaltStrike
5K Followers 32 Following Official account for Cobalt Strike. Benchmark red teaming tool known for its flexibility and powerful user community. Follow for new releases and other updates.
Forrest Orr @_ForrestOrr
4K Followers 526 Following Red Teamer, low level coding extremist and malware researcher. Windows exploit writer and bug hunter
kmkz @kmkz_security
19K Followers 2K Following Offensive Security, pom-pom girl... Who cares ?? Bourbon Offensive Security Services | BOSS
Eiriel @KLINIX5
4K Followers 579 Following
winterknife 🌻 @_winterknife_
4K Followers 5K Following low-level developer with a focus on 𝙸𝚗𝚝𝚎𝚕 𝚡𝟾𝟼 ISA devices running 𝚆𝚒𝚗𝚍𝚘𝚠𝚜 | R&D @BHinfoSecurity | https://t.co/lyJL0y7qRZ
spotheplanet @spotheplanet
11K Followers 144 Following Hacking the planet at https://t.co/ifUgKQtEYV. Buy me a vinyl at https://t.co/SO41y55HJL
Walied Assar @waleedassar
5K Followers 642 Following Reverse Engineer / Malware & Vulnerability Researcher / SOC Analyst / Pharmacist / Fisherman
CCob🏴�... @_EthicalChaos_
9K Followers 437 Following Ceri Coburn: Hacker | R̷u̷n̷n̷e̷r̷ DIYer| Vizsla Fanboy and a Little Welsh Bull apparently 🏴 Author of poorly coded tools: https://t.co/P6tT2qQksC
Arno0x0x @Arno0x0x
2K Followers 120 Following The difference between stupidity and genius is that genius has its limits.
Matt Miller @epakskape
12K Followers 649 Following Killing bug classes and breaking exploits as part of @msftsecresponse. Adding more entropy to the Internet. https://t.co/J8GCGurGP3