Search results for #ReverseShell
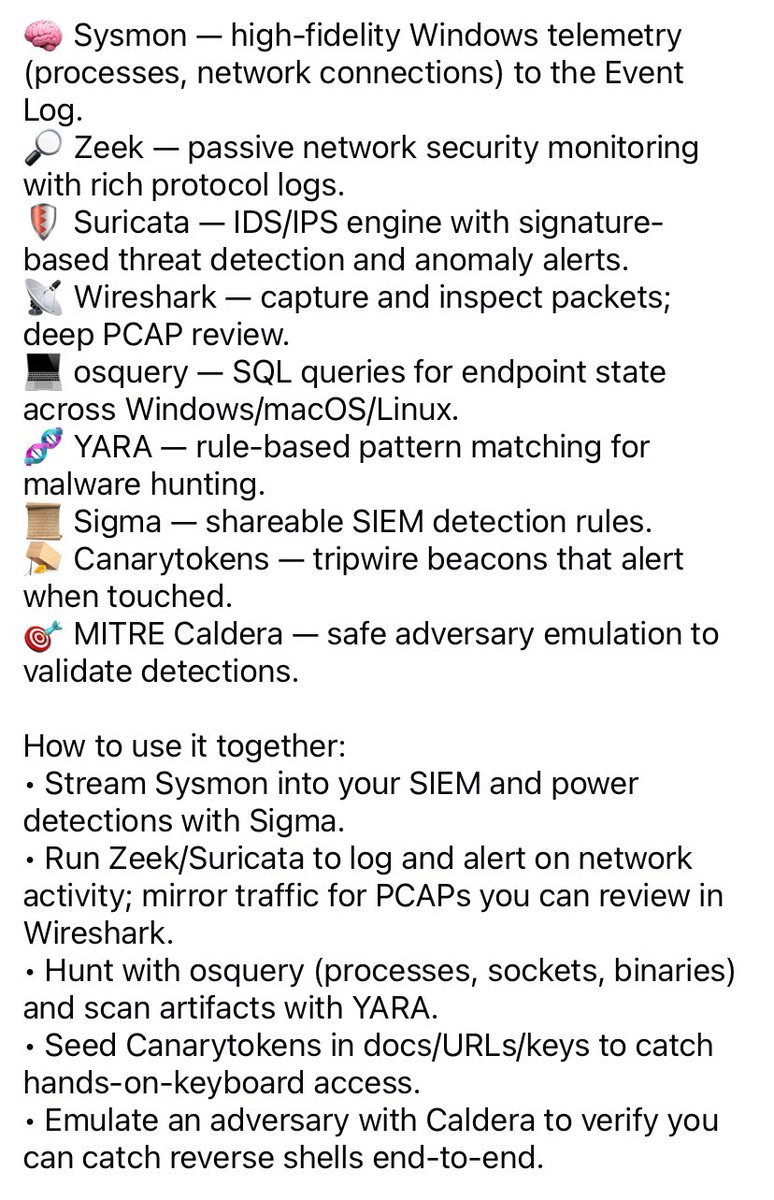
Reverse Shell Detection & Defense 🔒 Build a blue-team lab stack to spot C2 callbacks, suspicious outbound shells, and post-exploitation activity. For lab, training and defensive use only. #BlueTeam #ThreatDetection #ReverseShell #Wireshark #infosec #DFIR #SOC #CyberSecurity
Después de mucho tiempo.. Nueva herramienta y entrada en el #blog!🙃 NekoDNS: Jugando con DNS una vez más: darkbyte.net/nekodns-jugand… NekoDNS - Experimental Reverse DNS Shell: github.com/JoelGMSec/Neko… #Darkbyte #Hacking #DNS #ReverseShell #NekoDNS
Hackers can abuse .pyz (Python ZipApp) files to hide malicious code and trick victims into opening them. A single click could give attackers remote access to your device. youtube.com/shorts/lvMPw0p… #CyberSecurity #EthicalHacking #ReverseShell #WhatsApp #InfoSec #Awareness
Acesso al servidor mediante Reverse Shell. thewhiterabbit.es/obtencion-de-a… #hacking #pentesting #reverseshell
Walkthrough of Pyrat TryHackMe CTF: port scanning exposed HTTP on port 8000, reverse shells gained access, .git repo revealed creds for SSH, and privilege escalation via Python script and password brute-force. #TryHackMe #ReverseShell #CTFChallenge ift.tt/heKi8Sr
🚨 New Writeup Alert! 🚨 "VulnOS: Chronos Lab Walkthrough — Hack & Ye Shall Receive " by Aditya Bhatt is now live on IW! Check it out here: infosecwriteups.com/e683b176e3ce #reverseshell #ctfwriteup #polyglot #ctf #cybersecurity
🚨 New Writeup Alert! 🚨 "Pyrat TryHackMe Walkthrough: Step-by-Step Beginner’s Guide to Easy Level CTF with Reverse Shell and…" by Prajwal is now live on IW! Check it out here: infosecwriteups.com/df93f824d9d5 #beginnersguide #reverseshell #privilegeescalation #tryhackmewalkthrough…
Spent the afternoon running some controlled penetration testing labs, simulating reverse shell scenarios across separate networks using Flipper Zero’s BadUSB functionality. #CyberSecurity #PenTesting #RedTeam #ReverseShell #FlipperZero #Hackazillarex
⚠️ Important: This guide is for educational use only. Never use reverse shells on unauthorized systems. Always obtain explicit permission before conducting any testing. #ReverseShell #PenetrationTesting #CyberSecurity #EthicalHacking #InfoSec #RedTeam #Netcat
A #reverseshell is a type of #networkcommunication where the #targetmachine (the victim) initiates a connection back to an #attacker’s machine. This is in contrast to a standard shell, where the attacker would connect to the target machine and execute commands.
It was a fun machine to #hack. #hacker #hacking #wordpress #reverseshell tryhackme.com/room/internal?… #tryhackme @RealTryHackMe aracılığıyla
I just published 🕵️♂️ Document based malware analysis- Click to Exploit: Office Docs, Macros & 👑Emotet medium.com/p/%EF%B8%8F-%E… #MalwareAnalysis #ReverseShell #Emotet #ThreatIntel #DFIR #CyberSecurity #KaliLinux
Built a tiny .exe today. Gave it my IP and port. It reached out, we bonded. Now I control its whole system. Friendship goals.🌝😶🌫️ #ReverseShell #Metasploit
How to weaponize powershell script into exe with undetectable method. hack a computer with easy method. youtu.be/J_cowBN8hmU #EthicalHacking #BatToExe #CyberSecurity #Shorts #ReverseShell #HackingAwareness #Infosec #RedTeam #WindowsSecurity
I created a simple c# backdoor youtu.be/smbOcmsABfM #CSharpBackdoor #EthicalHacking #ReverseShell #PowerShellPayload #RedTeam #CyberSecurity #PenetrationTesting #HackingTutorial #OffensiveSecurity
🚨 New Blog Alert: Using Azure Virtual Machines as a Netcat Reverse Shell 🔗 infophreak.com/using-azure-vi… #infophreak #cloud #reverseshell #pentesting #redteaming #azure #cybersecurity #cybersecuritytraining #infosec #ethicalhacking
🔍 SOC analysts look for: • Outbound connections on uncommon ports • Command-line processes spawning unexpectedly • Base64 or obfuscated payloads in logs Catch it before the attacker starts digging. #ReverseShell #BlueTeamOps #SOCMonitoring #CyberDefense #scorpion_drogon
and post-exploitation steps using Metasploit. ⚠️Reminder: Always perform tests ethically and in controlled environments. #CyberSecurity #EthicalHacking #ReverseShell #Metasploit #KaliLinux #InfoSec #Pentesting #CaptureTheFlag #HomeLab
Ejemplo de como convertir un código de Python que contiene una reverse shell a un ejecutable .exe indetectable por el antivirus. #python #reverseshell #informatica #coding #linux #pentesting
github.com/ekomsSavior Disclaimer: only test on systems you have permission to test on. User assumes all risks. #hacker #python #reverseshell #linux #exploit

irtiza mehdi @REVERSESHELL_
17 Followers 73 Following Cybersecurity Analyst | Intrusion Researcher | I detect the undetectable | ~HackerOne
ReverseShell @revers3shell
12 Followers 181 Following Ciberseguridad | Privacidad es un derecho 💻 | Compartiendo consejos, noticias y hacks para proteger tu información 🛡️ | Apasionado por el ethical hacking
SHELL @REVERSESHELL88
2 Followers 25 Following
Reverseshell @Nadeem0431
1 Followers 113 Following